We can all agree that the internet is a godsend, yes? Thanks to the wonders of technology over the past decade, we’ve been using it to connect with people, buy things, and even run businesses without having to leave the house.
However, all this convenience does have a dark side. With most of us becoming increasingly dependent on online applications and platforms, it’s also more challenging to protect our privacy and security. This is especially true if you have small children. Younger internet users are often unaware of the dangers lurking around on the web, after all.
While there is no substitute for constant vigilance, there are a handful of steps you can take to maintain your privacy and your family’s safety online:
1. Install a good antivirus software on your devices.

Come on, this should be a given. A good antivirus program doesn’t just protect your devices from, well, viruses. It can also alert you to suspicious websites and block harmful pop-up ads.
2. As much as possible, don’t connect to public wi-fi hotspots.

As a colleague of mine likes to say, there’s no such thing as a free lunch. Public wi-fi is a great example.
Sure, they’re attractive in a pinch, but those hotspots in libraries, airports, and shops aren’t encrypted like your connection at home. Thus, anyone can grab unencrypted data packets so long as they’re within the signal’s reach. Worse still, some malicious people can set up their own rogue wi-fi to look like public hotspots, just so they can steal yours and your family’s data.
If you really must use public wi-fi, surf with a VPN or try to encrypt the wi-fi signal. Most of all, don’t log into any financial or social media accounts while you’re at it.
3. Look out for suspicious emails – and teach your children to recognize them.

You’ve heard of the Nigerian prince emails, right? You know, the ones that claim to be from African royalty eager to wire you millions of dollars in exchange for helping them out with a small fee?
Most of us know better than to fall for that, but phishing emails have gotten craftier. Some scammers have been able to replicate bank or company logos quite well, making their emails look more convincing.
Remember that these organisations will never ask for your log-in details or your account information through email. Also, check the email addresses and the URL links. If they look especially fishy, delete the email. You should teach your kids not to click on attachments from emails like this too. They could infect your device with a virus that could then make it vulnerable to attacks.
4. Use strong passwords.

There’s a reason why a lot of websites encourage you to use numbers, uppercase, and lowercase letters for your passwords. These precautions simply make it harder for people to hack into your account.
And in case you still don’t know, “password” and “123456” are the most common passwords. Please, please don’t use them.
5. Opt for two-factor authentication.

Sometimes, the strongest password comes for naught if a hacker manages to break into a website’s password database. This is where two-factor authentication or 2FA comes in.
Apart from your password, 2FA makes use of another form of verification that relies on something only you have access to. For instance, one of the most common 2FA methods is where a site or service sends an access code to your mobile phone after you log in with your password.
This extra layer of security ensures that you are actually the one trying to log in, and not just anyone who managed to guess your password.
6. Avail of a VPN.

Short for “virtual private network,” a VPN directs your data to a distant server via an encrypted tunnel. This is a lot safer than your data leaving the home network and going directly onto the open webs.
Best of all, it prevents your internet service provider from snooping. Sadly, some of them have been known to track their users and then sell their data.
7. Be wary of app permissions.
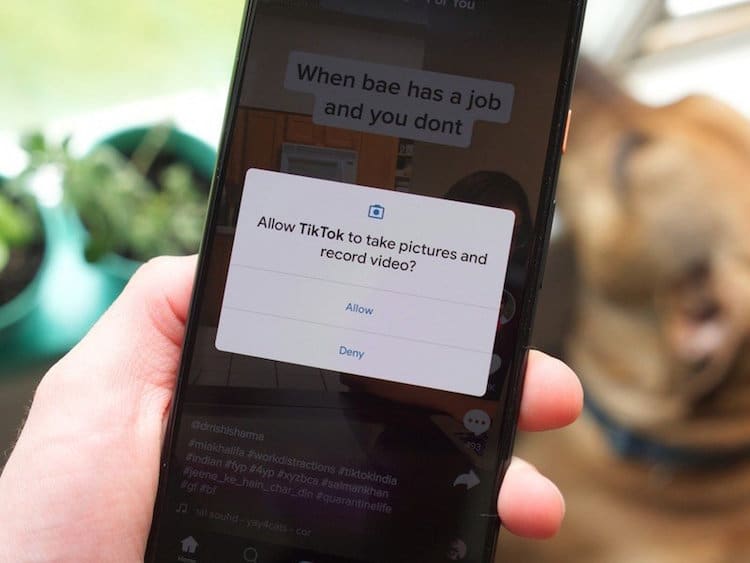
Image Credit: android.com
If a photo-editing app requests permission to your photo library, that’s not so shady. However, if an app is seeking the same for access to things that don’t make sense, that’s a red flag.
For example, if you downloaded, say, a newspaper app and it requested access to your microphone and camera, then it can be used to spy on you.
Look before you leap, basically.
Lastly, be careful of who you let into your databases or social media accounts. No, I’m not talking about your partner. (Personally, I wouldn’t hand over my social media passwords to mine, but I digress.) In this case, I’m pertaining to the remote workers you hire.
The majority of Filipino remote workers are diligent, capable, professional, and are extremely loyal if you treat them well. On the other hand, it’s hard to predict what a disgruntled employee might do, so it’s important to take some extra measures.
At Remote Staff, though, we screen all of the Filipino talents that make it into our diverse talent pool. We also have standard NDA’s and contracts so that our clients can hire amazing people with peace of mind.
Click here and schedule a callback with us today.
Serena has been working remotely and writing content for the better part of the last decade. To date, she's written for Pepper.ph and Mabuhay Magazine, among others, and has churned out more than a thousand articles on everything from The Basics of Stock Market Investing to How to Make Milk Tea-Flavored Taho at home. Hermits, aspiring hermits, and non-hermits with interesting project propositions may email her at serena.estrella10@gmail.com.
























 Zero Recruitment Fee
Zero Recruitment Fee